
GYTPOL’s CEO and Co-Founder, Tal Kollender, was just a teenager when she became exposed to hacking.
It was not long before she realized the impact it had if applied in both a good or a bad way, and drove her to want to learn everything about it and become an accomplished “hacker”.
During her mandatory army service in Israel, she was chosen to serve in one of the leading cyber units. The experience and training she received is unrivalled anywhere in world which is why Israel has become well known as the Start-Up Nation for Cybersecurity. During her work experience she noticed that there were no tools available to address security gaps caused through misconfigurations. For each company Tal worked for, she needed to repeatedly write her own tools.
This is where the GYTPOL idea came about. To provide a robust, enterprise tool which would allow organizations to “Think Like A Hacker”, whilst gaining visibility of the security gaps which hackers exploit all the time when breaching organizations, but to also remediate them too.
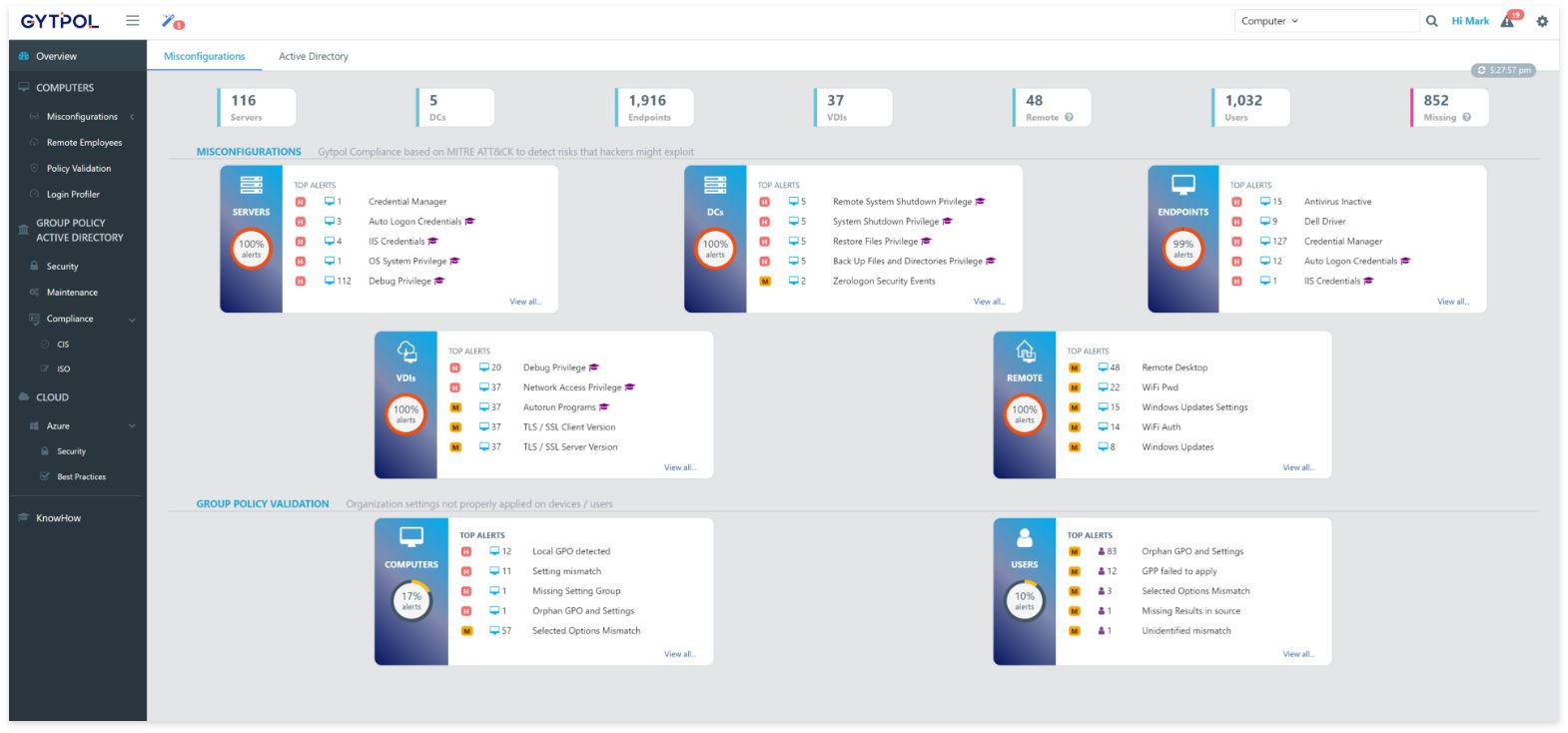
GYTPOL is a Security Configuration Management platform that detects OS security gaps due to misconfigurations such as human errors and default settings. Endpoints are the entry-points for hackers and securing them with just EDR is not enough.
Organizations have always lacked the much-needed visibility of misconfigurations on endpoints/servers. Today, it is addressed using a manual best-effort approach process. Even when identified, organizations are continually challenged to remediate without causing any impact and then being able to validate if their actions have been fully successful. Overall, it is a time consuming, resource intensive activity with limited accuracy and success.
Security Configuration Management
Address Misconfigurations
GYTPOL has created the only Security Configuration Management platform, Validator, to finally address misconfigurations. It provides continuous detection on all devices, at all times using a very low resource, low touch approach. Even remote non-VPN connected devices are supported. What’s more, it has a game changing full remediation suite which includes:
- Automatic capabilities for newly added devices
- Zero impact to business operations. Nothing gets broken, no reboots required
- Revert back to previous state if needed
User Cases
- Preventing endpoint breaches through misconfigurations
- Ensuring security baselines are secure with the latest hardening requirements
- Validating Group Policies are applied on all endpoint devices
- Continuous audit and healing for regulatory compliance on all devices (CIS, NIS, ISO etc)
- Detection of lateral movement
- Detection of Active Directory misconfigurations
GYTPOL is offered as either on-prem or SaaS and is very simple to deploy (in under 30 minutes), whilst providing an easy-to-use dashboard which can also be integrated with a SIEM.
GYTPOL offer a free trial where you can see for yourself why the solution is already deployed in hundreds of companies, supporting over 2.5 million devices including Fortune 200 companies and public sector organizations.