Move Beyond SIEM?
The Hunters SOC platform empowers security teams to automatically identify and respond to incidents that matter across their entire attack surface, at a predictable cost.
Through built-in detection engineering, data correlation, and automatic investigation, Hunters helps teams overcome volume, complexity, and false positives, mitigating real threats faster and more reliably than SIEMs, ultimately reducing customers’ overall security risk.
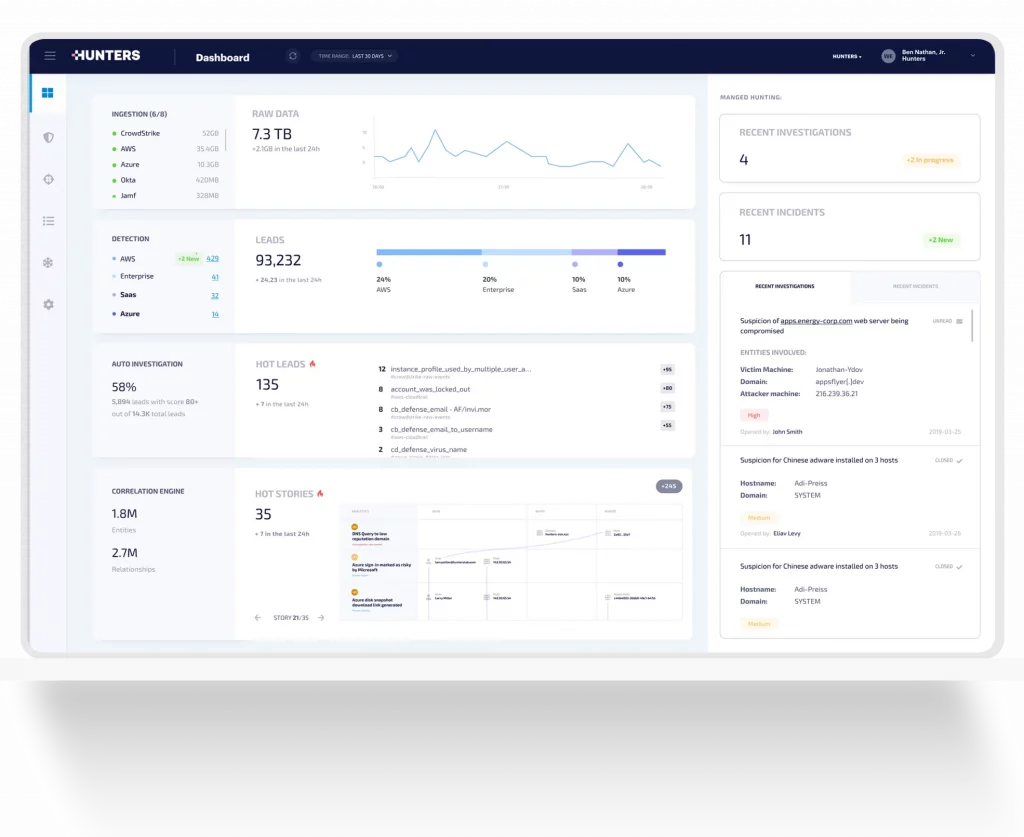
Today, SOCs waste time with an overwhelming amount of telemetry data to correlate, tools to manage, and false positives to chase. Data is siloed across SIEMs, security and IT products, enterprise data, threat intelligence and TTPs.
There’s lots of heavy lifting to keep all the data, signals and alerts from across the attack surface organized and mapped. Meanwhile, security teams are constantly updating their own playbooks to keep up with the methodologies attackers are using to investigate behaviour, security teams need to stitch everything together, a nearly impossible task—like looking for a needle in a haystack.
This means security teams can’t separate the “noise” from real incidents, making the attack surface more vulnerable and putting the business at risk. And, this never-ending, manual work is frustrating and tedious, resulting in high turnover of prized security analysts who are exhausted from daily “firefighting”
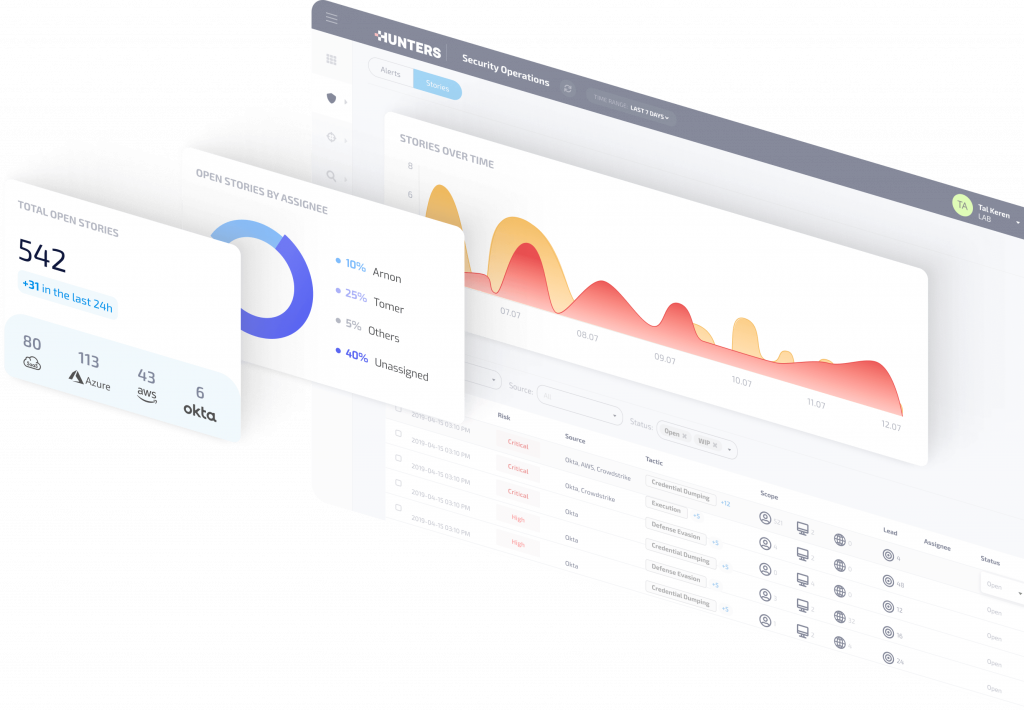
-
Attack Surface Coverage
Vendor-agnostic, unlimited data ingestion and normalization across all data sources at a predictable cost -
Empowered Security Teams
Built-in detection engineering, data correlation, and automatic investigation help SOC overcome volume, complexity, and false positives -
Reduced Security Risk
Reduce overall security risk and compliance exposure by mitigating real threats faster and more reliably than when using SIEM
What do you imagine your security teams and business could accomplish by automatically finding and responding to incidents that matter across your attack surface?